
The British signals and cyber intelligence headquarters, GCHQ.
UPDATED with House reaction WASHINGTON: US leaders and experts expressed dismay at the British government’s announcement today that it would only restrict — not forbid — the use of “high-risk vendors” — preeminently China’s Huawei — in the nation’s networks. The battle is certain to continue, with the UK under pressure from both the US and China and with detailed legislation yet to come before Parliament.
“The United Kingdom’s decision to put short-term economic interests above the long-term security considerations for an entire alliance is highly disappointing and sends exactly the wrong signals to the world at exactly the wrong time,” said Andy Keiser, a former Trump transition staffer and veteran House intelligence staffer. “I expect the effort to compel London to change its mind as part of a bilateral trade negotiation with the United States begins today.”

Rep. Adam Smith, chairman of the House Armed Services Committee
UPDATE Another call for Britain to reconsider came this afternoon from the Congressmen who serve as US delegates to the NATO parliamentary assembly: House Armed Services member Rep. Mike Turner, a Republican, and Foreign Relations Committee member Rep. Gerry Connolly, a Democrat.
“We are extremely concerned by the news that the United Kingdom will allow Chinese company Huawei to help build the country’s 5G data network,” Turner and Connolly said in a statement. “China’s ability to control Chinese companies such as Huawei poses a potential critical threat to telecommunications and privacy. This decision by the UK puts the US-UK shared intelligence at risk of being compromised by China. We urge the UK to immediately reconsider its decision and instead put a total ban on Huawei’s involvement in the UK’s building of its 5G data network.”
And on Tuesday evening came another lament from House Armed Services Committee chairman Rep. Adam Smith and the ranking Republican, Rep. Mac Thornberry. “The U.K.’s decision to allow Huawei a role in building parts of its 5G network is troubling,” their statement said. “While the U.K. believes that they can mitigate the risk posed by Huawei’s access to their network, in 5G there is no sure way to isolate the core network from other components. Granting Huawei access to any part of a country’s network opens access to the whole network, providing a potential door to the Chinese government. This decision will inevitably complicate America’s ability to share information with our closest ally.” UPDATE ENDS
 Five Eyes ‘Infected’?
Five Eyes ‘Infected’?
What’s the worst-case scenario that Thornberry and Smith are hinting at? A compromise to the ultra-sensitive Five Eyes intelligence-sharing arrangement between the US, the UK, and fellow Anglophone allies Australia, Canada, and New Zealand.

Sen. Ben Sasse
“Here’s the sad truth: Our special relationship is less special now that the U.K. has embraced the surveillance state commies at Huawei,” seethed Sen. Ben Sasse, a Republican member of the Senate Intelligence Committee, in a statement this morning. “The Chinese Communist Party has infected Five Eyes with Huawei, right at a time when the US and UK must be unified in order to meet the global security challenges of China’s resurgence.”
One of the experts who has helped find what appear to be deliberate backdoors in Huawei firmware agreed with Sasse. “As a former intelligence official, I would agree with Ben Sasse that we and our Five Eyes partners should not cozy up to China in order to save a few pennies,” said Terry Dunlap, a former NSA hacker and co-founder on cybersecurity firm ReFirm Labs. Dunlap’s team and other security firms found vulnerabilities in Huawei firmware at far higher rates than any other company’s products.
But Britain’s Secretary of State for digital, culture, media and sport (DCMS), Baroness Nicky Morgan, dismissed worries over Five Eyes, saying those systems are far removed from the limited foothold Huawei will be allowed.

The Rt Hon Baroness Nicky Morgan
“Nothing in the Review’s conclusions affects this country’s ability to share highly sensitive intelligence data over highly secure networks, both within the U.K. and with our partners, including the Five Eyes,” the minister said in an official statement to the House of Lords. “GCHQ” – General Communications Headquarters, the British equivalent of the NSA — “have categorically confirmed that how the UK constructs its 5G and full fibre public telecoms networks has nothing to do with how the Government shares classified data.”
That’s missing the point, argued Nicholas Eftimiades, a former senior US senior intelligence officer and China expert who’s written regularly on Chinese espionage for Breaking Defense. “It is a threat to any communications between the nation states,” he told me. “Much coordination, diplomacy, and non-classified information sharing is done through open communications.”
Once you let Huawei run any substantial portion of your network, Eftimiades continued, they can use their foothold in secondary systems to affect critical functions. “Embedded hardware in a national communications infrastructure provides the opportunity to delay and manipulate data,” he said. “For example, because stock trading is done in milliseconds by artificial intelligence, financial markets could be easily be manipulated by delaying data for even just fractions of a second.”
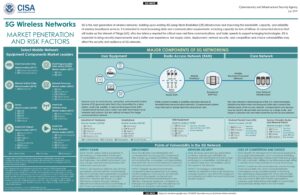
Department of Homeland Security summary of 5G cybersecurity issues
Core Wars
The core of the issue is the core of the network. If you allow Huawei and other high-risk vendors to provide peripheral functions – up to 35 percent of network equipment, according to the UK’s official guidelines published today – can you keep them out of the core functions that would compromise security? Or does the increasingly blurry distinction between core and periphery, and the insidious nature of computer infiltration, mean that cyber cancer anywhere could metastasize to the whole network?
“The UK decision to separate Huawei access between core and non-core stands in stark contrast to the far more prudent approach taken by Australia,” said Bryan Smith, who’s served in intelligence agencies and the both intelligence committees on the Hill. “Australia has concluded that 5G networks will be designed so that the sensitive functions currently performed only in a ‘core’ …. will gradually move closer to the ‘edge.’ The 5-G edge, consisting of radio antennas and base stations, could prove to be just as vulnerable to hard-to-detect attacks that could exfiltrate, reroute, or duplicate sensitive data.”

Ian Levy
The British government insists you can still draw a clear line and defend it. “It’s continuous, long term work,” wrote Ian Levy, a veteran of General Communications Headquarters – GCHQ, the British equivalent of NSA – and technical Director of the National Cyber Security Centre, in a blog post published today. “We don’t get to say ‘no core, 35% access, home in time for tea!’”
“In previous networks, sensitive functions were grouped together in a couple of locations we called ‘core,’” Levy wrote. “In 5G they are spread out a bit more, but sensitive functions are still sensitive functions and you can put your arms round them – for example, we list them in the guidance published today”: 24 separate items for 5G alone, from Authentication Server to Wireline Access Gateway.
“Our risks and mitigations are not determined by the concepts of ‘core’ and ‘edge’; these have always been convenient labels to hide complexity,” Levy continued. “Instead, through properly identifying the attack vectors, we can work out the sensitivity…of specific functions and assets and apply appropriate controls and mitigations.”
“If your network design means that you need to run really sensitive functions processing really sensitive data (i.e. core functions) on an edge access device on top of a bus stop, your choice of vendor is the least of your worries and you probably shouldn’t be designing critical national infrastructure,” Levy said. “The thing to take away is that the NCSC really does understand how these networks will work, the limits of how they can evolve and what we need to do to protect them properly.”
How will the UK do that? For both 5G and fiber-optic networks – but not for existing 4G networks – Baroness Morgan explained the government has decided that “high risk vendors should be:
- excluded from all safety related and safety critical networks in Critical National Infrastructure;
- excluded from security critical network functions;
- limited to a minority presence in other network functions to a cap of up to 35%; and
- subjected to tight restrictions, including exclusions from sensitive geographic locations.”
Nor will telecommunications companies be able to implement these guidelines at their discretion. Instead, they’ll be subject to NCSC approval and, ultimately, new laws. “These new controls will also be contingent on an NCSC-approved risk mitigation strategy for any operator using such a vendor,” the Baroness said. “The Government intends to bring forward legislation, at the earliest opportunity, to limit and control the presence of high risk vendors in UK networks.”

Huawei HQ in Shenzhen, China
A Foot in the Door
The UK’s narrow focus on technical matters misses China’s much larger strategy, which intertwines technology, commerce, espionage, military power, and political influence, our experts argued.
“They get their foot in the door via the subsidized pricing and then continue to eat away at the incumbent,” Dunlap told me. “As a result, the eventual switching costs you would face from a non-subsidized replacement option are huge.”
“Slowly over time more and more pieces of communications gear will be replaced by Huawei gear,” Dunlap continued. “Your security is controlled by the vendor, who may or may not choose to fix certain vulnerabilities. I guess that can be said about any vendor — but not all vendors have their government as a business partner.”
Huawei has a close relationship with the government – its founder was formerly in the People’s Liberation Army – but it’s hardly unique among Chinese tech firms. While China is largely a capitalist economy, the state retains enormous influence and practices an official policy of “civil-military fusion,” both through informal connections (guanxi) and through official policies, such as a law requiring companies to hand over data to security agencies on request.
“In approving Huawei, the UK has made a critical mistake based on expediency and short-term cost,” Eftimiades said. “China is the world’s most aggressive nation conducting economic espionage. Allowing China continued access to communications infrastructure provides unprecedented access to commercial trade secrets and intellectual property.”
“China’s policy is long-term,” Dunlap said. “They tend to think in terms of decades and not months or weeks like us Westerners. In fact, their vision is so long-term that you and I may not live long enough to see the day Huawei completely owns the UK’s (and other countries) communications infrastructure. It’s just a matter of time.”
Sullivan says Ukraine supplemental should cover all of 2024, long-range ATACMS now in Ukraine
“We now have a significant number of ATACMS coming off their production line and entering US stocks,” Jake Sullivan said today. “And as a result, we can move forward with providing the ATACMS while also sustaining the readiness of the US armed forces.”


























